A Decentralized Architecture for Visual Forensics
Introduction
Swarm-based image detection offers a powerful new approach to visual forensics. Instead of relying on a single model to assess whether an image is real, tampered, or fabricated, this architecture distributes the work across many lightweight, specialized agents. Each agent analyzes only part of the image or focuses on a specific kind of feature, allowing the system to detect subtle inconsistencies and reach a collective judgment.
This concept draws inspiration from biological intelligence systems—like ant colonies or neural networks—where individual agents work independently but form accurate conclusions when their insights are combined.
User Interface Concept
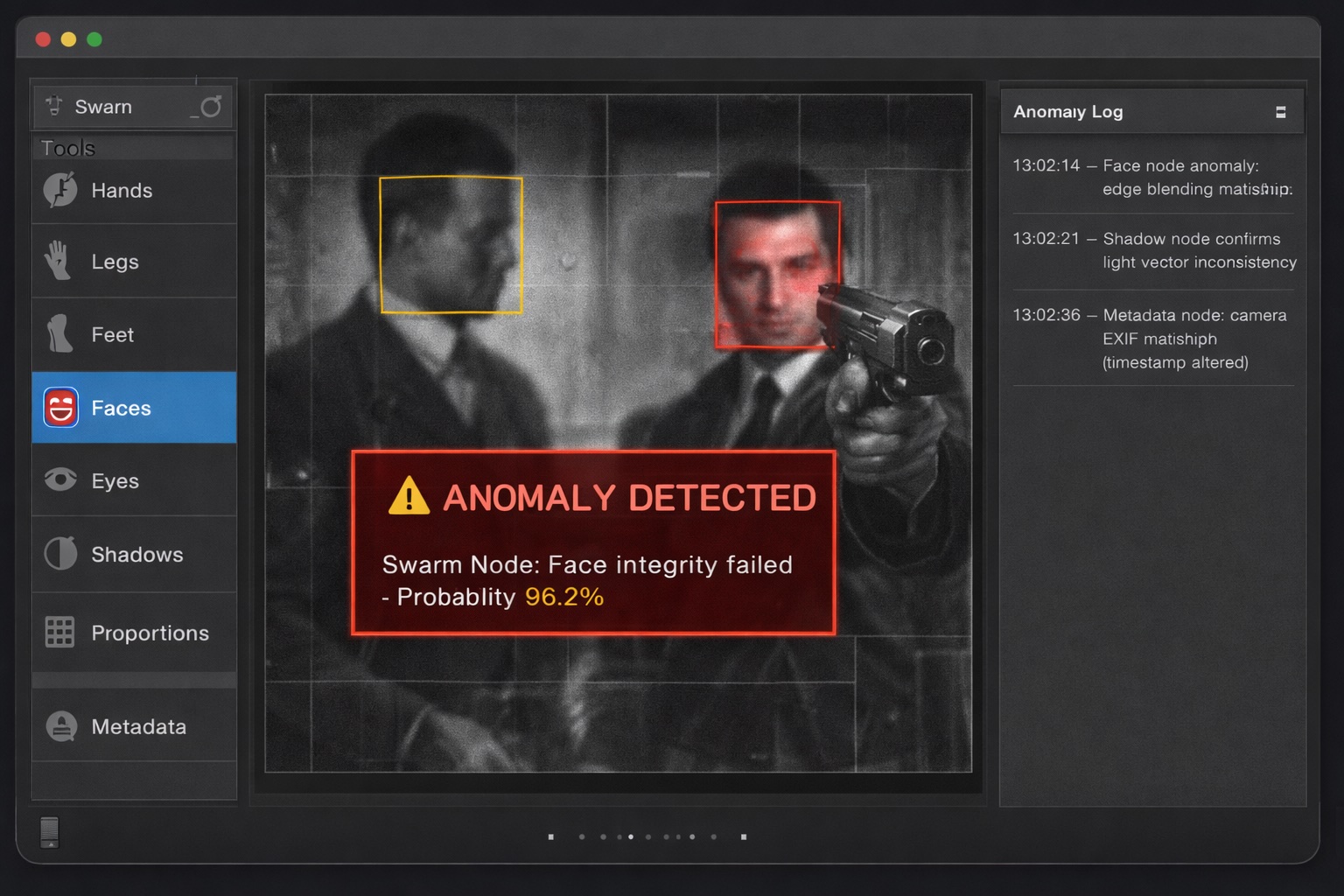
The user interface resembles a digital forensics workbench. On the left, a palette of detection modules allows the user to activate or focus on particular elements—hands, legs, faces, shadows, and other components. In the center, an image is displayed under investigation. If the swarm of agents detects something suspicious, an alert appears over the image reading “Anomaly Detected” in red.
This simple layout hides a powerful, multi-agent system running behind the scenes.
Workflow Overview
-
Image Decomposition
The system begins by breaking down the image into semantic regions. These include body parts, textures, lighting, shadows, metadata, and more. Each region is assigned to a group of agents with domain-specific expertise.
Typical agents exchange information with each other through back or forward propagation ie. upstream or downstream.
Swarm Agents take a cure from nation they don’t propagate forward or backward but contribute to a central store much like bees contributing to a HoneyComb. -
Specialized Detection Agents
Each agent applies focused detection models to its assigned region. These models may look for:
-
Facial symmetry irregularities
-
Lighting and shadow inconsistencies
-
Pixel-level noise mismatches
-
GAN-generated artifact patterns
-
Metadata inconsistencies, such as altered EXIF tags
-
Reflection and refraction logic violations
-
-
Consensus Mapping
-
Once agents perform their analysis, they contribute to a common store. If multiple agents detect anomalies in a particular region, their findings reinforce each other. The system builds a confidence map that highlights areas with potential tampering or forgery.
-
Anomaly Flagging
When consensus reaches a threshold (e.g. 95% confidence of falsification), a visual alert is triggered. This includes:
-
A highlighted region on the image
-
A label describing the anomaly (e.g. “shadow mismatch” or “GAN edge artifact”)
-
A numeric confidence score
-
In video workflows, an optional timestamp for when the anomaly occurs
-
Why Use a Swarm Architecture?
Swarm-based models offer several key advantages:
-
Resilience: No single point of failure. If one agent is incorrect, others can correct or outweigh it.
-
Parallelism: Agents work asynchronously, allowing rapid analysis on distributed systems.
-
Modularity: New detection modules can be added without retraining the entire system.
-
Transparency: Results can be traced to localized decisions, making the system more auditable.
Traditional monolithic classifiers struggle with nuanced manipulations. Swarm-based detection embraces complexity and breaks it into manageable, specialized tasks.
Potential Applications
This architecture has wide-reaching implications:
-
Deepfake detection in political and social media videos
-
Tamper forensics for legal evidence and law enforcement
-
Authenticity verification for journalistic or historical photos
-
Security screening in government or enterprise systems
-
Multiplayer game validation (detecting falsified positional data)
-
Astronomical or remote sensing anomaly classification
Final Thoughts
Swarm-based detection is not just an upgrade to existing forensic tools—it’s a shift in thinking. Rather than searching for a universal truth in a manipulated world, this system allows hundreds or thousands of agents to each notice what seems slightly off. Their combined intuition uncovers the truth.
You’re not building a single algorithm. You’re building a collective suspicion engine.
.